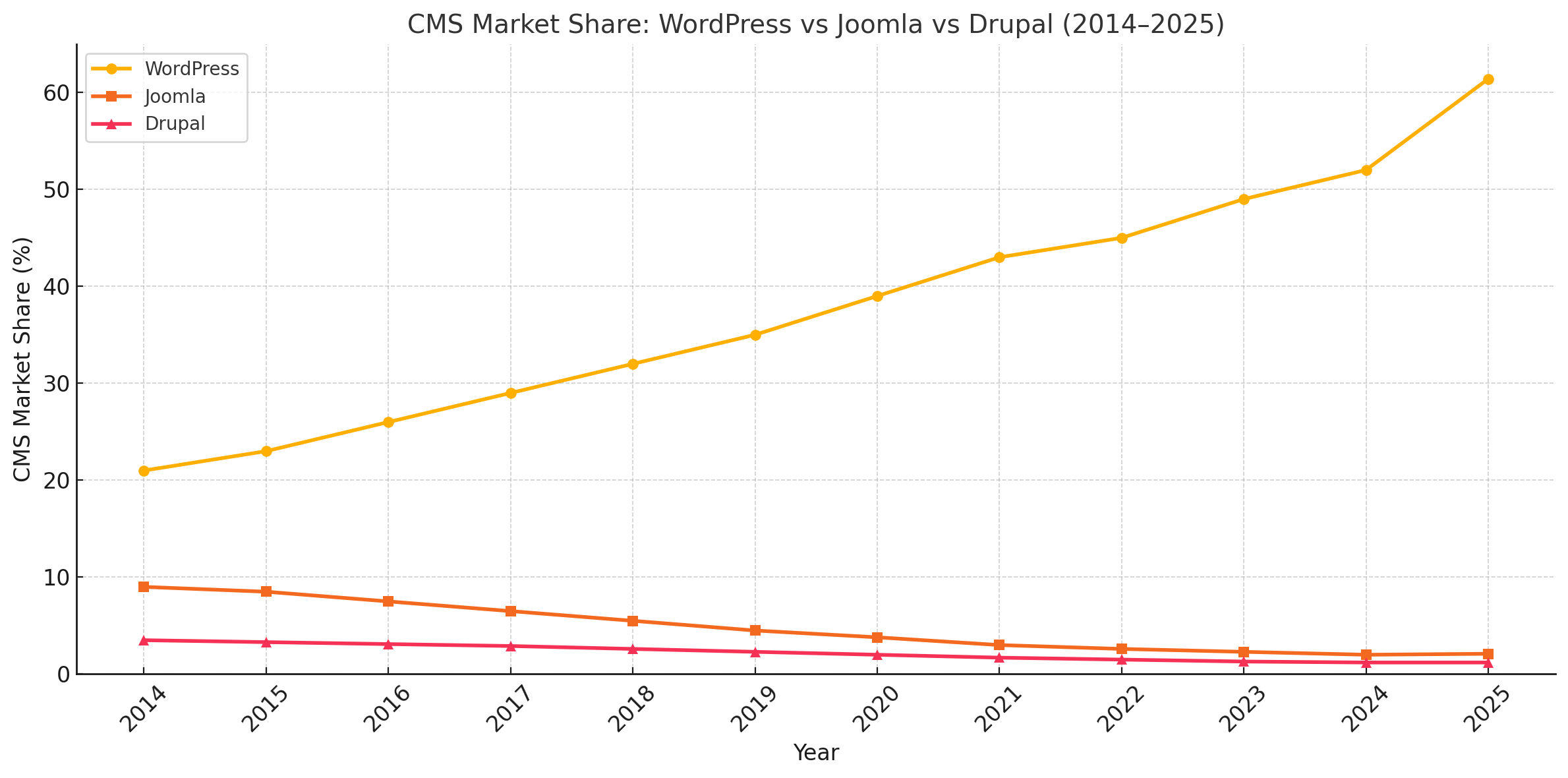
Major WordPress Vulnerability Categories
- SQL Injection (SQLi)
- Attackers inject malicious SQL queries through unsanitized input fields, gaining access to databases, user credentials, or site content.
- Example: Old WordPress versions before 4.8.3 (2017) had SQLi flaws in the
$wpdb->prepare()function.
- Cross-Site Scripting (XSS)
- Malicious scripts injected into websites, often via comments or poorly coded plugins/themes.
- Common in plugins like WP GDPR Compliance (2018) and Slider Revolution (2014).
- Privilege Escalation
- Bugs that allow attackers to elevate their access (e.g., from subscriber → admin).
- Example: REST API vulnerability (2017, WordPress 4.7.0/4.7.1) allowed unauthenticated users to modify posts.
- Remote Code Execution (RCE)
- Attackers upload or execute arbitrary code. Usually comes from plugin/theme flaws.
- Example: File Manager plugin (2020) let unauthenticated users upload and execute PHP files.
- Authentication Bypass
- Weaknesses in login/auth functions letting attackers impersonate users.
- Example: WordPress 5.7 (2021) had an object injection vulnerability in PHPMailer that could lead to bypass in some configurations.
- Cross-Site Request Forgery (CSRF)
- Tricks users into performing unwanted actions while authenticated.
- Found often in plugins like Yoast SEO (2015).
- File Upload Vulnerabilities
- Poor validation allows attackers to upload malicious files (e.g., PHP shells).
- Example: Gravity Forms (2016) suffered from a file upload issue.
Notable WordPress Vulnerabilities by Year
- 2014: Slider Revolution Vulnerability
- A premium plugin bundled with many themes. Severe flaw allowed attackers to download sensitive files (
wp-config.php), leading to mass exploits.
- A premium plugin bundled with many themes. Severe flaw allowed attackers to download sensitive files (
- 2015: Cross-Site Scripting in WordPress Core
- Versions <4.2.1 had a critical XSS flaw that allowed attackers to compromise millions of sites.
- 2016: REST API Issues & Plugin Flaws
- Multiple XSS and file upload vulnerabilities reported. The W3 Total Cache plugin exposed database information.
- 2017: REST API Content Injection (WordPress 4.7.0/4.7.1)
- Allowed attackers to modify posts without authentication. Over 1.5 million sites defaced before patch.
- 2018: GDPR Compliance Plugin
- 100,000+ sites vulnerable to privilege escalation + CSRF. Attackers could create admin accounts.
- 2019: Social Warfare Plugin RCE
- Popular plugin (70k+ installs) let attackers inject malicious scripts via reflected XSS → RCE.
- 2020: File Manager Plugin Vulnerability
- A zero-day flaw let anyone upload malicious PHP files. Exploited widely; affected 700k+ sites.
- 2021: WP Database Reset Plugin CSRF + Privilege Escalation
- Attackers could reset entire sites, lock out admins, and create rogue accounts.
- 2022: Elementor & Essential Addons
- Widely used site builder plugin had critical RCE and SQLi vulnerabilities, impacting millions.
- 2023: WooCommerce Payments Vulnerability
- Authentication bypass allowed attackers to impersonate admin users. Urgent patch issued.
- 2024 (recent): WP Automatic Plugin (200k installs)
- Zero-day RCE exploited in the wild. Attackers uploaded malicious PHP code to gain site access.
Summary
- Core WordPress is relatively secure today, thanks to fast patching and automatic updates.
- Plugins & themes remain the biggest attack surface, especially those with large install bases.
- Zero-days in popular plugins (File Manager, WooCommerce, Elementor, etc.) are the most exploited.
- Hardening strategies: keep WordPress, themes, and plugins updated; minimize plugin use; use WAF/firewalls; restrict file permissions.
Here are some of the most severe WordPress-related vulnerabilities from roughly the past decade—specifically, those assigned the highest CVSS (Common Vulnerability Scoring System) scores, indicating critical risk:
Top WordPress Vulnerabilities by CVSS Score
1. CVE-2023-5199 – PHP to Page plugin – CVSS 9.9
- Type: Authenticated (Subscriber+) Local File Inclusion leading to Remote Code Execution (RCE)
- Impact: A subscriber-level user can abuse a shortcode vulnerability to include and execute arbitrary files, potentially enabling full server compromise.
- Severity: One of the highest-ever scores for a WordPress plugin.
wordfence.com
2. CVE-2025-4394 – Alone – Charity Multipurpose Non-profit WordPress Theme – CVSS 9.8
- Type: Arbitrary file upload allowing Remote Code Execution
- Impact: Attackers could upload ZIP archives containing PHP backdoors, enabling full site takeover—including admin account creation, malware deployment, phishing redirects, etc.
- Note: Exploitation started on July 12, 2025, just two days before public disclosure, affecting approximately 200 live sites. Patched in version 7.8.5 on June 16, 2025.
TechRadar
3. CVE-2020-36837 – ThemeGrill Demo Importer plugin – CVSS 9.9
- Type: Authentication bypass that resets the database
- Impact: Attackers already authenticated can reset the site’s entire database—potentially wiping data and creating admin-level access.
SANS Institute
4. Other Critical CVSS 9.8-Rated Vulnerabilities
Numerous high-severity vulnerabilities (all scored at 9.8) have been identified within the last few years. Here are highlights:
- CVE-2019-25213 – Advanced Access Manager plugin allowed unauthenticated file reads (e.g.,
wp-config.php). - CVE-2019-25217 – SiteGround Optimizer plugin had Remote Code Execution and Local File Inclusion via auth bypass.
- CVE-2020-36832 – Ultimate Membership Pro plugin permitted unauthenticated logins as any user, including admins.
- CVE-2021-4443 – WordPress Mega Menu plugin enabled arbitrary file creation leading to RCE.
SANS Institute - CVE-2024-9265 – Echo RSS Feed Post Generator plugin allowed unauthenticated registration as administrator.
- CVE-2024-9289 – WordPress & WooCommerce Affiliate Program plugin had authentication bypass to login as admin.
- CVE-2024-5150 – Login with Phone Number plugin allowed unauthenticated login as any existing user.
SANS Institute+1 - CVE-2024-11642 – Post Grid Master plugin suffered from Local File Inclusion via
locate_template, enabling RCE. - CVE-2025-9636 – Post Grid & Gutenberg Blocks plugin allowed unauthenticated admin registration via privilege escalation.
- CVE-2024-13446 – Workreap theme plugin permitted takeover via account takeover.
- CVE-2024-11284 / 11285 / 11286 – WP JobHunt plugin had privilege escalation, email takeover, and auth-bypass issues—each scored 9.8.
- CVE-2025-2232 – Realteo (Real Estate Plugin) allowed unauthenticated admin account registration.
- CVE-2025-1771 – Traveler theme had Local File Inclusion enabling arbitrary file execution.
- CVE-2024-13560 – WP Foodbakery plugin allowed unauthenticated arbitrary file uploads and admin registration vulnerability.
SANS Institute
5. Additional Noteworthy High-Severity Plugins
- CVE-2024-10960 (Brizy – Page Builder) – Arbitrary file uploads (CVSS 9.9) leading to possible RCE.
- CVE-2024-12213 (WP Job Board Pro) – Privilege escalation to register as admin (CVSS 9.8).
Reddit+1 - CVE-2021-24284 – Kaswara Modern WPBakery Addons plugin enabled unauthenticated arbitrary file upload and code execution. Reportedly the CVSS was rated 10.0.
Reddit
Summary Table
| CVE ID | Component & Issue | CVSS Score | Impact Summary |
|---|---|---|---|
| CVE-2023-5199 | PHP to Page plugin – LFI → RCE via shortcode | 9.9 | Authenticated subscriber → RCE |
| CVE-2025-4394 | Alone theme – Arbitrary file upload → RCE | 9.8 | Full site takeover |
| CVE-2020-36837 | ThemeGrill Demo Importer – Auth bypass → DB reset | 9.9 | Site reset, admin access |
| Others (e.g., CVE-2019-25213, 2019-25217, 2024-11642, etc.) | Various plugins – File Inclusions, Privilege Escalation, Auth Bypass | 9.8 | Data exposure, admin account creation, RCE |
| CVE-2021-24284 | WPBakery Addons – Arbitrary upload → RCE | 10.0 | Complete site compromise |
Recommendations
- Plugins & Themes Are the Real Attack Surface
Almost all of these high CVSS issues stem from third-party plugins/themes, not WordPress core. - Minimize Risk by Keeping Software Updated
Always update plugins/themes immediately when patches are released. - Reduce Attack Surface
Use only necessary, well-reviewed plugins and themes. Delete unused ones. - Use Defense-in-Depth
Employ Web Application Firewalls (WAF), restrict file permissions, and monitor logs for anomalies.
CVE-2021-24284 – Kaswara Modern WPBakery Page Builder Addons
This vulnerability, rated CVSS 10.0, allowed unauthenticated arbitrary file uploads leading to code execution and full site compromise.
Scope of exposure:
- Estimated number of vulnerable sites: Between 4,000 and 8,000 WordPress installations still had the plugin active at the time of reports The Hacker NewsDark Reading.
- Sites targeted in attack campaigns: Security researchers observed that approximately 1.6 million websites were scanned in total, though the majority targeted were not actually running the vulnerable plugin BrandefenseSecurity Affairs.
- Wordfence noted that over 1,000 websites under their protection were still running the plugin and thus continually targeted The Hacker News.
Unfortunately, no publicly disclosed lists or identities of specific affected websites were available—likely due to privacy and the sensitive nature of security incidents.
Summary:
- Estimated vulnerable sites: 4,000–8,000 still installed the plugin.
- Total sites scanned in attacks: Around 1.6 million.
- Confirmed protected sites running the plugin: Over 1,000, tracked by Wordfence.
CVE-2023-5199 – PHP to Page Plugin
This vulnerability involved a Local File Inclusion (LFI) that could escalate to Remote Code Execution (RCE). It’s less clear which—or how many—websites were actually impacted.
Findings:
- I found no publicly available information naming specific affected sites or providing broad estimations of numbers affected.
- The known impact stems from the vulnerability leveraged by authenticated users (subscribers or above) using the shortcode—but no data on scale or reported attacks was available from the sources reviewed NVDwiz.io.
Summary Table
| CVE ID | Affected Websites / Scope of Impact | Notes |
|---|---|---|
| CVE-2021-24284 | ~4,000–8,000 still had plugin installed; ~1.6 million scanned | No specific site names disclosed; active exploitation observed |
| CVE-2023-5199 | No specific data available on affected sites | No published numbers or site identities |
Notes
While industry sources provide a strong sense of scale—thousands of vulnerable sites and millions scanned—they do not reveal actual site names or URLs affected, likely to protect site owners and avoid enabling further attacks.
1. How to Detect if a Site is Vulnerable
- Check Plugin/Theme Versions
- Look up the affected plugin/theme in the WordPress dashboard under Plugins → Installed Plugins or Appearance → Themes.
- Compare the installed version to the patched version from the vendor’s site or WordPress.org plugin directory.
- Example: For Kaswara Modern WPBakery Addons, the plugin was removed from WordPress.org and never patched → if installed, it’s vulnerable.
- Scan with Security Tools
- Tools like WPScan, Wordfence, or Sucuri SiteCheck can flag known vulnerable plugins/themes and outdated versions.
- Example WPScan command:
wpscan --url https://example.com --enumerate vp(--enumerate vpchecks vulnerable plugins)
- Server Log Inspection
- Look for suspicious requests (e.g., POST requests uploading
.phpfiles, or requests to/wp-content/uploads/). - Many mass-exploitation campaigns leave behind traces in
access.loglike:POST /wp-admin/admin-ajax.php?action=kaswara_ajax_upload
- Look for suspicious requests (e.g., POST requests uploading
2. Mitigation & Patch Strategies
- Immediate Actions
- Disable and delete vulnerable plugins/themes if no patch exists (like Kaswara).
- If a patch exists (e.g., Alone Theme CVE-2025-4394), update immediately.
- Harden WordPress
- Restrict file permissions:
wp-config.php→ 400 or 440/wp-content/uploads/→ disallow execution of PHP files via.htaccess:<Files *.php> deny from all </Files>
- Disable direct file editing in
wp-config.php:define('DISALLOW_FILE_EDIT', true);
- Restrict file permissions:
- Web Application Firewall (WAF)
- Cloudflare, Wordfence, or Sucuri WAF can block exploit signatures.
- Example: Wordfence blocked the Kaswara WPBakery exploit in July 2022 before it could execute.
3. Exploit Breakdown (Simplified Example)
Let’s take CVE-2021-24284 (Kaswara WPBakery Addons):
- Attacker sends a malicious POST request to vulnerable AJAX action (
kaswara_ajax_upload). - No authentication or nonce check is required.
- Attacker uploads a
.phpweb shell disguised as an image. - Attacker accesses the file directly via
/wp-content/uploads/…/shell.php. - Now they have remote code execution (RCE) → can add admin accounts, modify files, or pivot further into the server.
Actions:
- If the vulnerable plugin/theme is still installed, the site is exploitable.
- The safest action for unpatched plugins (like Kaswara) is removal, not just deactivation.
- Ongoing monitoring via WAF + log inspection is essential since many of these campaigns involve automated bots scanning millions of sites.
Keeping Track of WordPress Vulnerabilities and rogue plugins/themes
Here are the most trusted sources:
1. WPScan Vulnerability Database
- The most widely used public WordPress vulnerability database.
- Includes vulnerabilities in:
- Core WordPress releases
- Plugins
- Themes
- Each entry lists: CVE ID (if assigned), severity (CVSS score), description, affected versions, and fix status.
- Actively updated and also powers many security scanners.
2. Wordfence Threat Intelligence
- Commercial security vendor for WordPress.
- Provides blog advisories, real-time threat feeds, and detailed write-ups on actively exploited vulnerabilities.
- Often one of the first to spot mass exploitation campaigns (e.g., the Kaswara WPBakery Addons campaign).
3. Patchstack Database
- Another excellent vulnerability tracker, focusing on plugin and theme flaws.
- Each entry has severity ratings, exploitability details, and patch status.
- Patchstack also highlights “unpatched” plugins/themes that should be removed immediately — a big help in avoiding seriously bad plugins.
4. Sucuri Security Blog
- Regularly posts about active exploits and malware campaigns.
- Focuses more on real-world compromises than raw vulnerability data.
- Great for keeping track of what’s being exploited in the wild (not just theoretical risks).
5. NVD / CVE Details
- The U.S. government’s official CVE database.
- Useful for finding the official CVSS scores and technical details.
- Less WordPress-specific, but authoritative for severity and tracking.
“Bad Plugin” Watchlists
- Wordfence & Patchstack both maintain advisories about plugins that are either:
- Abandoned / removed from the WordPress.org repository
- Unpatched with known exploits
- Actively abused in malware campaigns
Examples of plugins often blacklisted:
- Kaswara Modern WPBakery Addons (CVE-2021-24284) → removed, never patched
- Slider Revolution (2014 LFI) → bundled with themes, long exploited
- WP File Manager (2020 zero-day RCE) → heavily targeted
Recommendation for site owners:
- Subscribe to WPScan or Patchstack vulnerability alerts (free tiers available).
- Use Wordfence Security plugin or similar, which automatically blocks exploit attempts.
- Regularly audit installed plugins/themes → remove anything unmaintained or flagged as unpatched.