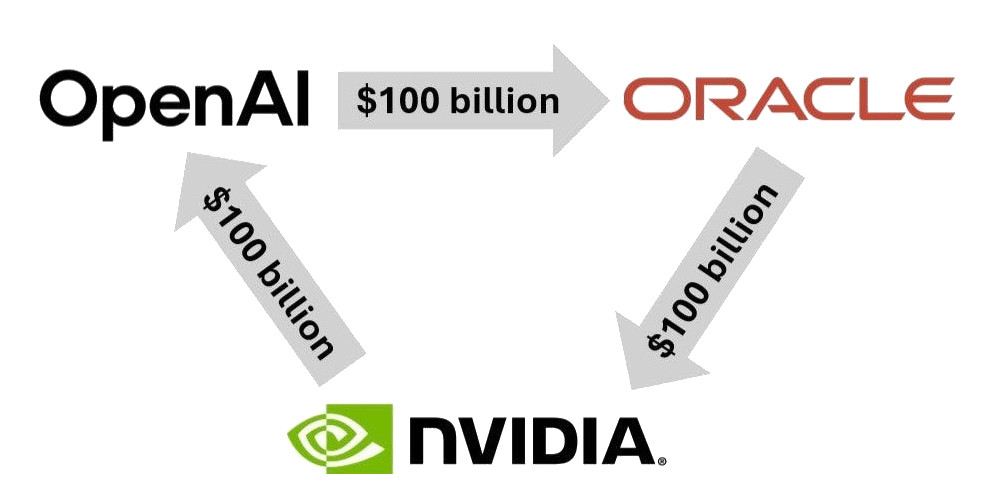
We’ve all seen the above image when Oracle started making waves about their AI contract to provide OpenAI compute power at their Abilene DC with tonnes of NVIDIA GPUs – well there’s now news about circular financing fraud involving the big AI players…
We look at what this article is saying and assess whether a postive circular financing fraud case will be the pin that bursts the AI bubble: https://substack.com/home/post/p-179453867
The Algorithm That Detected a $610 Billion Fraud: How Machine Intelligence Exposed the AI Industry’s Circular Financing Scheme
The article describes how advanced trading algorithms and machine intelligence detected an unprecedented $610 billion circular financing fraud involving major AI industry players, including Nvidia, Microsoft, OpenAI, Oracle, and xAI. This scheme involved companies repeatedly recycling the same money through chip purchases, cloud credits, and investments, allowing them to recognize fictitious revenue and inflate financial numbers without actual cash being exchanged.binance+3
What Happened
On November 20, 2025, AI-driven trading systems analyzed Nvidia’s earnings and discovered massive inconsistencies: billions in accounts receivable remained unpaid, and customers were taking longer to pay, resulting in aging bills and swelling inventories. The investigation revealed funds circulated between firms—such as Nvidia investing in xAI, which would use pushed loans to buy Nvidia chips, while Microsoft and Oracle funneled cloud credits through OpenAI—getting booked as revenue at multiple companies, but with no real payment behind the transactions.instagram+2
Impact on Financial Markets
Once the fraud was flagged, Nvidia’s stock, which had surged by $130 billion after earnings, quickly crashed as algorithms triggered selloffs faster than human analysts could respond. Bitcoin, used by many AI startups as loan collateral, also plunged as market confidence evaporated, with experts predicting further Bitcoin sell-offs as defaults increase.stockmarketanalysis04.substack+2
Industry Reactions and Fallout
Executives—including those from Airbnb and OpenAI—acknowledged the reliance on artificial “vibe revenue,” admitting the industry’s expected future profits were vastly overstated, and many projects would never deliver the anticipated returns. Famous investors quickly exited positions, and credit agencies are expected to downgrade the sector as payment cycles lengthen and the circular financing unwinds.news.futunn+2
Warnings and Criticism
Analysis of the reports cautioned that while some claims align with public financial data, other details appear speculative or exaggerated, casting doubt on the scale and specifics of the fraud presented in the article. However, the exposure of circular accounting practices has sparked renewed scrutiny of AI industry finances and the systemic risks they pose to both tech and broader financial markets.x+1
What would be the market implications if the fraud is confirmed?
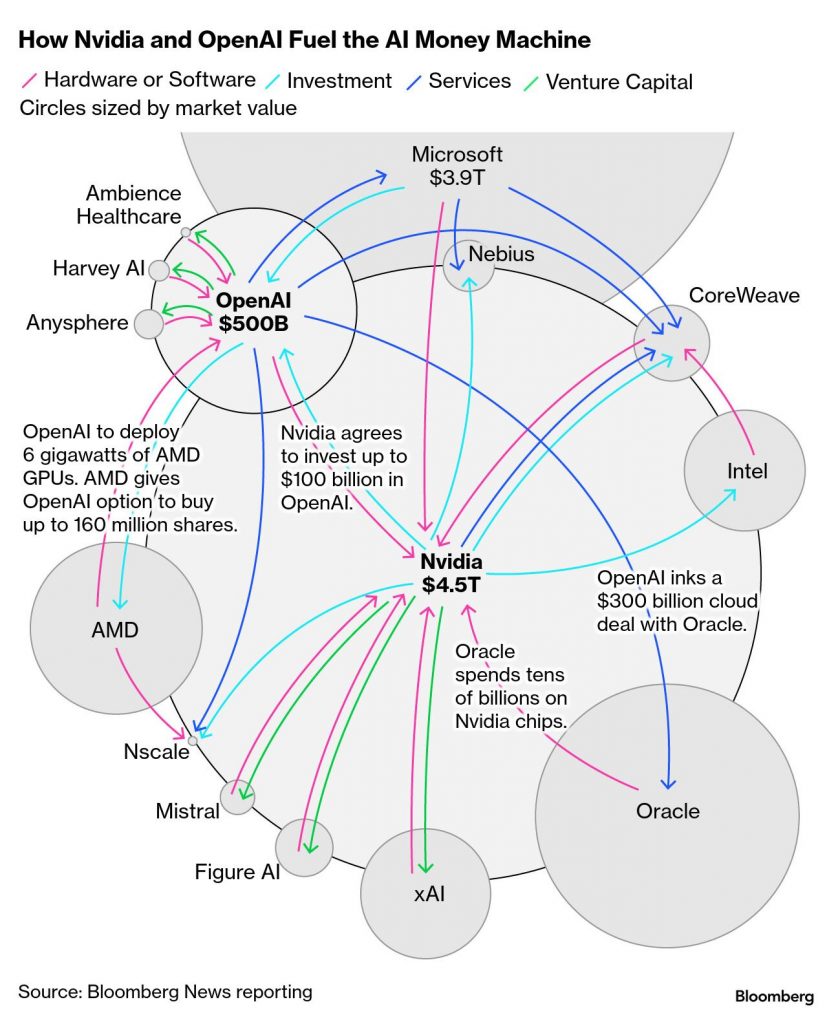
If the $610 billion AI industry fraud is confirmed, the market implications would likely be severe and multifaceted:
- Stock prices of the companies involved would likely experience sharp declines, similar to historic fraud cases where stock prices dropped significantly upon fraud discovery and investigation announcements. For example, firms have seen cumulative abnormal returns fall by 29% at fraud discovery and further 8% after regulatory investigation announcements, particularly when fraud involves revenue recognition or asset overstatement.nacva+1
- Investor trust across the AI and related tech sectors would erode drastically, causing not only plummeting stock demand for the implicated companies but also collateral damage to wider market confidence. This loss of trust can depress sales, revenue, and overall financial performance beyond the direct fraud perpetrators.financemagnates
- Increased regulatory scrutiny and enforcement actions would follow, including potential SEC investigations, fines, and legal consequences for perpetrators, shaking market stability and inviting tighter oversight on AI industry financial reporting.fraud+1
- The revelation of such a large-scale circular financing scheme would raise concerns over information opacity and systemic risks in the AI sector and adjacent markets. This could raise the risk of future stock price crashes and long-term market volatility due to shaken investor confidence and greater caution toward AI-related investments.sciencedirect
- Credit downgrades and withdrawal of investment capital across affected companies and startups would likely accelerate, hampering innovation financing and causing a sector-wide funding crunch.binance
Together, these effects imply a potential market shock comparable to major corporate fraud scandals, with profound short-to-medium term disruptions in AI industry valuations and investor behavior, and increased regulatory and due diligence focus on AI sector financial transparency.nacva+2
Which peer firms and sectors would face contagion risk?
If the $610 billion AI industry fraud is confirmed, the peer firms and sectors facing contagion risk would include:
- Other major AI and technology firms interconnected via investments, chip sales, and cloud services, such as Microsoft, Oracle, OpenAI, and Nvidia’s competitors. Because the fraud involved circular financing among these players, their financial health and market valuations would be at risk of contagion through direct exposures and reputational damage.
- The broader technology sector, including semiconductor manufacturers, cloud infrastructure providers, and AI startups, which depend heavily on investment flows and customer confidence linked to the implicated firms. Funding shortages and tighter credit conditions would ripple across these linked companies.
- Financial institutions such as banks, investment funds, hedge funds, and insurers holding equity, debt, or derivatives tied to AI and tech firms. Market shocks from the fraud revelation could trigger liquidity strains, asset fire sales, and valuation drops across these financial intermediaries.
- Sectors with strong dependence on AI-driven growth or technology investments, including software service companies, cloud computing, and innovative tech hardware industries, which would face heightened volatility and funding risks from cascading investor withdrawals.
In summary, the contagion risk would span a network of interlinked AI/tech firms, their financial backers (banks, funds, insurers), and adjacent sectors relying on AI-driven growth and innovation capital. These risks would be amplified by dense financial linkages, cross-holdings, and overlapping investor exposure, potentially escalating systemic risks and market instability across these interwoven sectors.ecb.europa+2
How likely is this a fraud?
The likelihood of this $610 billion AI industry fraud being real appears mixed, with some evidence supporting concerns but also significant skepticism about the full scale and details.
- Support for fraud possibility: Automated algorithms detected unusual circular financing flows and discrepancies in accounts receivable, payments, and inventory levels among key players like Nvidia, OpenAI, Microsoft, and Oracle. Executives and industry insiders have acknowledged artificial revenue recognition practices, “vibe revenue,” and unsustainable burn rates, fueling suspicions of inflated financial reporting and reliance on self-referential capital cycling.reddit+2
- Skepticism: Several data points in the original fraud claim articles do not fully align with official financial statements or audited reports. For example, some growth rates and cash conversion claims appear unverified or exaggerated, and robust revenue projections remain in place for major firms like Nvidia. Critiques suggest parts of the narrative may be speculative or amplified to support short-selling or competitive narratives.news.futunn+1
- Market actions such as large insider sales, stock volatility, and algorithmic trading responses reflect real concerns but do not alone prove deliberate fraud.
Overall, while there is credible reason for regulatory scrutiny and investor caution, it is not yet conclusively proven that a $610 billion-scale fraud has occurred as portrayed. Financial markets and regulators will need to conduct thorough audits and investigations to confirm or refute the full extent of circular financing and unverifiable revenues in the AI sector.reddit+1
What additional evidence would confirm or refute the fraud claim?
To confirm or refute the $610 billion AI industry fraud claim, the following additional evidence would be critical:
- Detailed audit reports and forensic accounting analyses that reveal whether reported revenues and assets align with actual cash flows, eliminating circular financing and fictitious transactions. Clear documentation of payment trails and verification of accounts receivable would be vital.
- Access to internal communications, contracts, emails, and loan agreements showing intent, knowledge, or concealment of fraudulent practices among the companies involved. These would demonstrate deliberate misrepresentation rather than innocent errors.
- Independent verification of inventories, customer payments, and cloud credit usage that purport to back financial figures, to detect any discrepancies or inflated valuations.
- Testimonies or whistleblower accounts from insiders who can provide direct evidence of deception, revenue manipulation, or artificially inflated accounts.
- Examination of algorithmic data and trading patterns that initially flagged the fraud, corroborated by hard financial evidence to remove speculation.
- Legal scrutiny and regulatory investigations with power to compel document production and testimony, leading to formal findings of fraud based on a balance of probabilities.
These types of evidence collectively would build a persuasive case by proving the key elements of fraud: false statements of fact, knowledge of falsity, intent to deceive, reliance on the falsehood by others, and resulting financial damage.lincolnandrowe+3
Due to the big players involved, how like is this to be recognised as fraud?
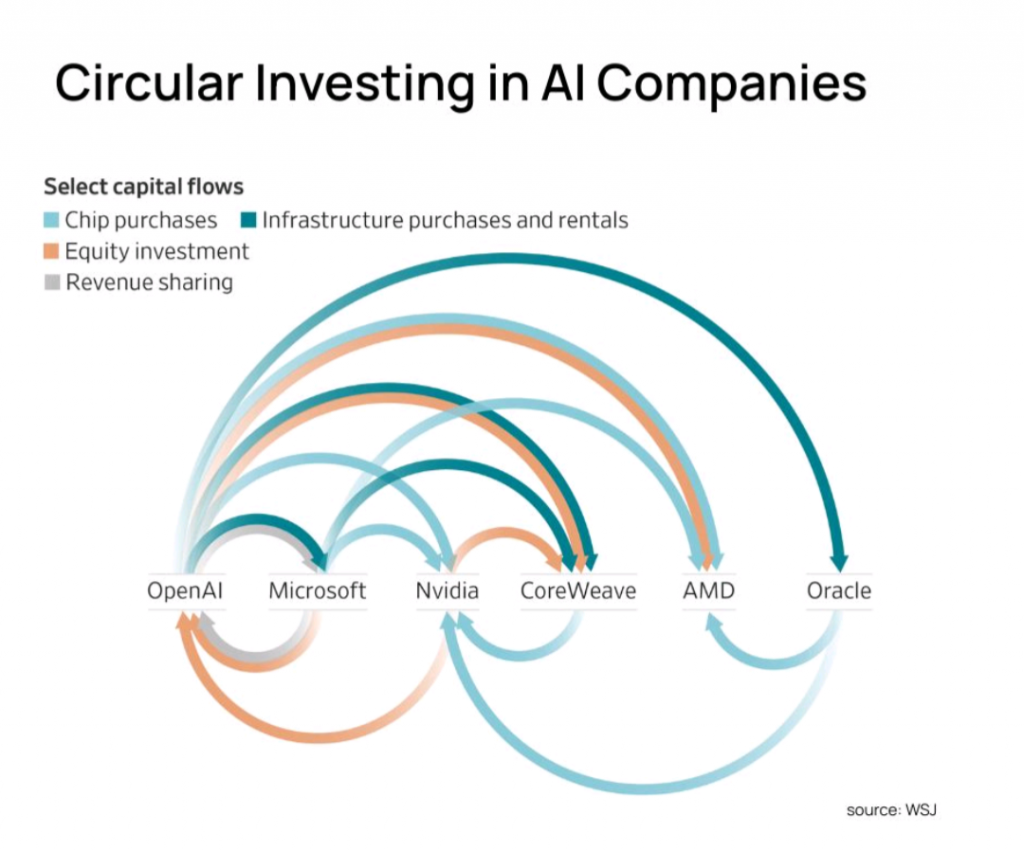
Given the involvement of major public companies such as Nvidia, Microsoft, Oracle, and OpenAI, it is relatively less likely that the alleged $610 billion circular financing scheme would go unrecognized or uninvestigated by regulators, auditors, and independent analysts. These firms operate under strict financial reporting standards, are subject to continuous market scrutiny, and have audits performed by reputable firms. Nvidia, for example, is audited by PwC and rated highly by credit agencies, and recently reported strong revenue guidance despite allegations.news.futunn+1
However, the complexity and scale of circular financing and vendor financing deals—spread across multiple firms and private entities like OpenAI—and the extraordinary sums involved create challenges in transparency. Given the high stakes, any material misstatements or abuses would likely draw regulatory attention from bodies like the SEC, and investigations would follow, as evidenced by past fraud cases in tech and finance.peterwildeford.substack
Market reactions such as rapid stock sell-offs, insider selling, and investor withdrawals suggest heightened suspicion and the potential for increased scrutiny. But actual recognition of fraud depends on whether clear evidence emerges proving intent and knowing misrepresentation, beyond complex but possibly legitimate financial engineering.substack+1
Therefore, while these large players’ reputations, audit requirements, and regulator oversight make outright fraud recognition more probable than in less regulated sectors, proving the full scope involves thorough forensic audits and investigations. The high-profile nature ensures any verified fraud will be highly publicized and swiftly acted upon.tomtunguz+3
The public seems to be able to see this circular financing already, but there has been no obvious denies or evidence until now?
The public’s ability to observe the circular financing is likely due to the following:
- Many of the so-called circular financing deals in AI are part of legitimate strategic partnerships, vendor financing, and ecosystem-building efforts. Companies like Nvidia, OpenAI, Microsoft, AMD, Broadcom, and others are deeply intertwined financially and operationally, investing heavily in each other through chip sales, equity stakes, and cloud infrastructure deals. This creates a “circular economy” that keeps capital flowing within a compact network, which is visible in market disclosures and company announcements but can appear as circular funding to outside observers.forbes+2
- These circular arrangements often reflect business models designed to ensure long-term demand for AI hardware and cloud services while fostering innovation through close alliances. While they may inflate revenue temporarily on paper by recognizing sales within the network, such practices are also common vendor financing strategies used in many industries historically and are not necessarily fraudulent if transparently disclosed and compliant with accounting standards.reddit+1
- Until now, there has been no obvious denial or strong rebuttal partly because companies benefit from these arrangements to drive AI ecosystem growth and financial performance, and the accounting treatments remain within legal frameworks. The lack of clear external evidence against them also means regulators and auditors have not formally challenged these practices as fraudulent yet, despite increasing scrutiny and skepticism among investors and algorithms detecting anomalies.bbc+1
- The recent algorithmic detection of potential fraud has heightened attention and raised the stakes for transparency, but distinguishing aggressive vendor financing from deliberate fraud requires detailed forensic audit evidence and regulatory investigation.
Thus, the public is seeing signals of circular financing because it is foundational to how AI ecosystem finance currently operates, but formal fraud recognition demands deeper proof beyond visible financial flows circulating within interconnected big players.ubs+3